捕获时间
2009-2-10
病毒摘要
该样本是使用“ VC ”编写的蠕虫程序,由微点主动防御软件自动捕获,采用“PEtite”加壳方式试图躲避特征码扫描,加壳后长度为 “29,396字节”,图标为“ ”,使用“exe”扩展名,通过“网页木马”、“文件捆绑”、“移动存储介质”等途径植入用户计算机,运行后下载其他木马到本地运行。 ”,使用“exe”扩展名,通过“网页木马”、“文件捆绑”、“移动存储介质”等途径植入用户计算机,运行后下载其他木马到本地运行。
感染对象
Windows 2000/Windows XP/Windows 2003
传播途径
文件捆绑、网页木马、可移动存储介质
防范措施
已安装使用微点主动防御软件的用户,无须任何设置,微点主动防御将自动保护您的系统免受该病毒的入侵和破坏。无论您是否已经升级到最新版本,微点主动防御都能够有效清除该病毒。如果您没有将微点主动防御软件升级到最新版,微点主动防御软件在发现该病毒后将报警提示您发现“未知木马”,请直接选择删除处理(如图1);
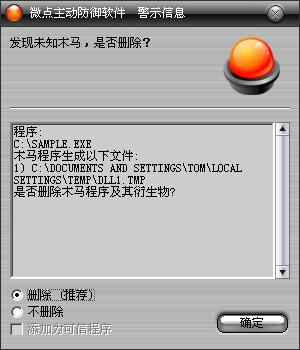
图1 微点主动防御软件自动捕获未知病毒(未升级)
如果您已经将微点主动防御软件升级到最新版本,微点将报警提示您发现"Worm.Win32.AutoRun.klb”,请直接选择删除(如图2)。
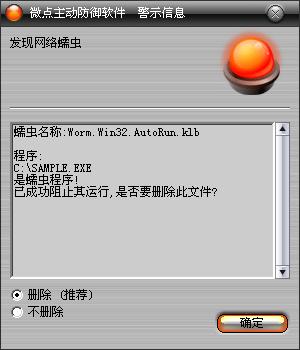
图2 微点主动防御软件升级后截获已知病毒
对于未使用微点主动防御软件的用户,微点反病毒专家建议:
1、不要在不明站点下载非官方版本的软件进行安装,避免病毒通过捆绑的方式进入您的系统。
2、建议关闭U盘自动播放,具体操作步骤:开始->运行->gpedit.msc->计算机配置->管理模板->系统->在右侧找到"关闭自动播放"->双击->选择"已启用"。
3、尽快将您的杀毒软件特征库升级到最新版本进行查杀,并开启防火墙拦截网络异常访问,如依然有异常情况请注意及时与专业的安全软件厂商联系获取技术支持。
4、开启windows自动更新,及时打好漏洞补丁。
病毒分析
(1)、删除指定的金山组件并释放指定的病毒衍生物
(2)、尝试结束指定的安全进程并停止指定服务
(3)、查找指定的360注册表项,找到后进行特定的修改实现对360监控的关闭
(4)、关闭指定关键字的窗口
(5)、对大部分安全软件进行映像劫持
(6)、修改文件的隐藏显示
(7)、访问指定网络连接下载其他木马到本地运行
(8)、对各个磁盘进行创建特定的AUTO文件,实现自动传播
病毒删除文件:
D:\Program Files\Kingsoft\Kingsoft Internet Security 2008
\kasbrowsershield.dll
%System32%\mfc71.dll
病毒创建文件:
%ProgramFiles%\ ALS.pif
%System32%\dllcache\linkinfo.dll
%Temp%\dll[随机数字].tmp
%System32%\mfc1.dll
c:\AUTORUN.INF
c:\ZNZ.PIF
病毒结束进程
avp.exe
360Safe.exe
360tray.exe
360rpt.EXE
Runiep.exe
Rsaupd.exe
RAv.exe
RSTray.exe
CCenter.exe
RAVMON.exe
Ravservice.EXE
ScanFrm.exe
rsnetsvr.exe
RavTRAY.exe
RavMonD.exe
RsAgent.exe
GuardField.exe
Ravxp.exe
GFUpd.exe
kmailmon.exe
kavstart.exe
KAVPFW.EXE
kwatch.exe
kav32.exe
kissvc.exe
病毒停止服务:
Sharedaccess
McShield
KWhatchsvc
KPfwSvc
Kingsoft Internet Security Common Service
Symantec AntiVirus
norton AntiVirus server
DefWatch
Symantec AntiVirus Drivers Services
Symantec AntiVirus Definition Watcher
Norton AntiVirus Server
病毒删除服务:
RavCCenter
RsScanSrv
RavTask
RsRavMon
病毒关闭窗口:
监视
监控
后门
NOD32
Process
瑞星
木马
杀马
绿鹰
Mcafee
Firewall
Virus
Anti
Worm
SREng
清理
下载者
病毒删除注册表:
项:
| |
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Minimal\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\SYSTEM\ControlSet001\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\CurrentControlSet\Control\SafeBoot\Minimal{4D36E967-E325-11CE-BFC1-08002BE10318}
HKLM\SYSTEM\CurrentControlSet\Control\SafeBoot\Network\{4D36E967-E325-11CE-BFC1-08002BE10318} |
|
项:
| |
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Run
键值:360Safetray
键值:360Safebox
键值:KavStart
键值:vptray
键值:ccApp
键值:RavTray |
|
病毒修改注册表:
项:
| |
HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\explorer\advanced\folder\hidden\showall
键值:CheckedValue
数据:2 |
|
项:
| |
HKLM\Software\360Safe\safemon
键值:ExecAccess
数据:0
键值:MonAccess
数据:0
键值:LeakShowed
数据:0
键值:SiteAccess
数据:0
键值:UDiskAccess
数据:0
键值:weeken
数据:0
键值:ARPAccess
数据:0
键值:IEProtAccess
数据:0
|
|
病毒创建注册表:
项:
| |
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360rpt.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safe.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360safebox.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\360tray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ANTIARP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ArSwp.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ast.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRun.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AutoRunKiller.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AvMonitor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.COM
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\AVP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\CCenter.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Frameworkservice.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GFUpd.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\GuardField.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\HijackThis.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\IceSword.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Iparmor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KASARP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kav32.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KAVPFW.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kavstart.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kissvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kmailmon.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KPfwSvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KRegEx.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVMonxp.KXP
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVSrvXP.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\KVWSC.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\kwatch.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Mmsk.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Navapsvc.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\nod32krn.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Nod32kui.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\PFW.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\QQDoctor.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAV.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMon.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavMonD.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Ravservice.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavStub.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RavTask.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RAVTRAY.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Regedit.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwmain.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwProxy.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rfwsrv.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rfwstub.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsAgent.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Rsaupd.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RsMain.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\rsnetsvr.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\RSTray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Runiep.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\safeboxTray.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\ScanFrm.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\SREngLdr.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojanDetector.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\Trojanwall.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\TrojDie.KXP
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPC32.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\VPTRAY.EXE
HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\Image File Execution Options\WOPTILITIES.EXE
键值:debugger
数据:%System32%\dllcache\spoolsv.exe |
|
病毒访问网络:
| |
http://m. w**8.com/tt.txt
http://m. w**8.com/dd/x.gif
http://m. w**8.com/dd/1.exe
http://m. w**8.com/dd/2.exe
http://m. w**8.com/dd/6.exe
http://m. w**8.com/dd/9.exe
http://m. w**8.com/dd/10.exe |
|
|
